gcc 4.6 appears to do the right thing.
2
gcc 4.8 appears to occasionally hang when compiling our generated code.
gcc have an
asm goto construct which ought to help with this.
Clang lacks this feature.
--Environment=... option appropriately
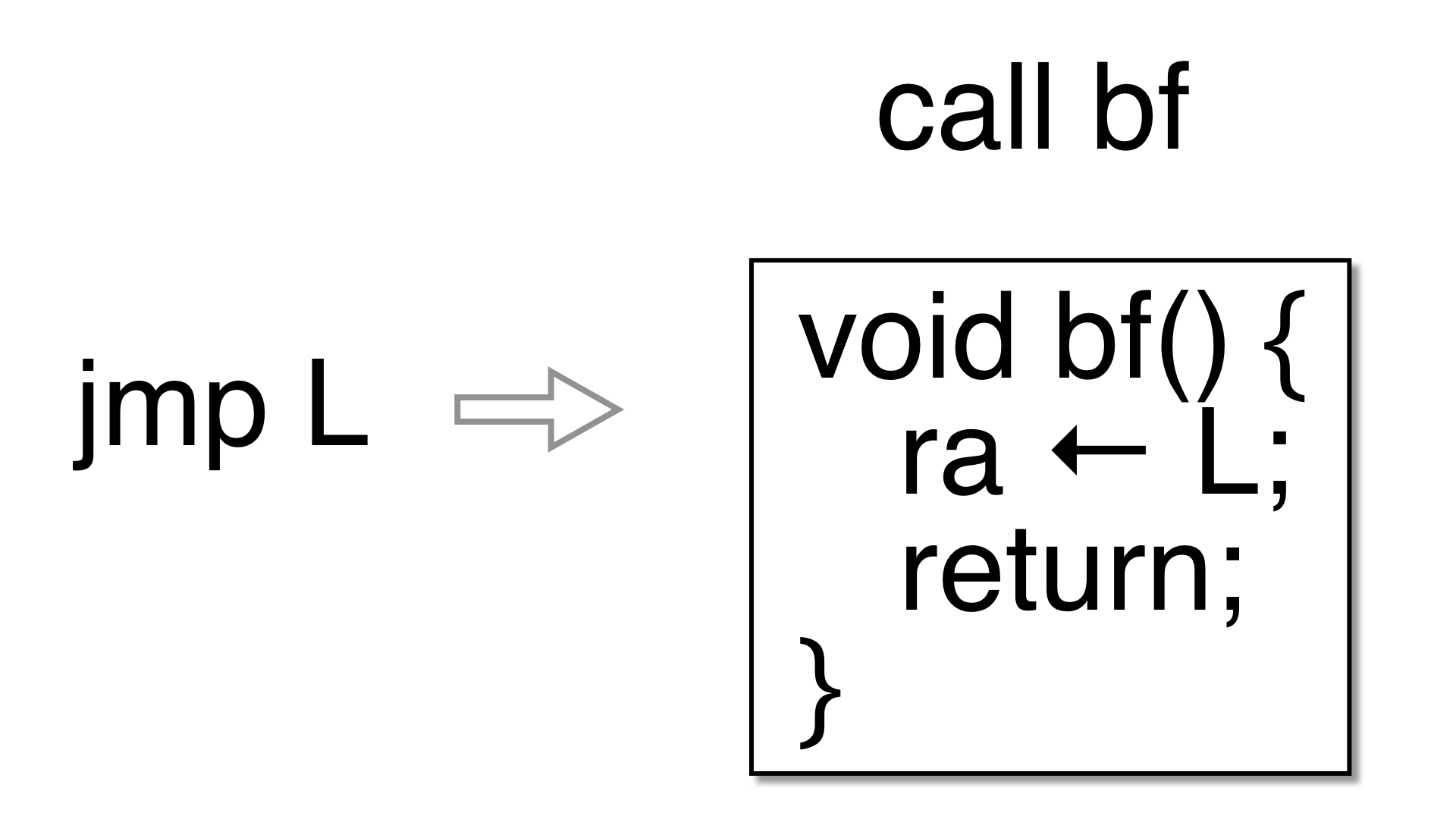
if you are going to use goto2push and goto2call and
test the generated code thoroughly. goto2push and goto2call
are turned off by default.