
If you are a student wanting to get into software protection or reverse engineering research, playing with Tigress is a great place to start! You ca use Tigress to learn how code obfuscation algorithms work, or you can generate arbitrarily complex reverse engineering challenge problems for yourself or your friends!
A good way to get started with software protection research is to pick up a copy of Surreptitious Software:

You should also check out our companion educational website, LigerLabs.org:
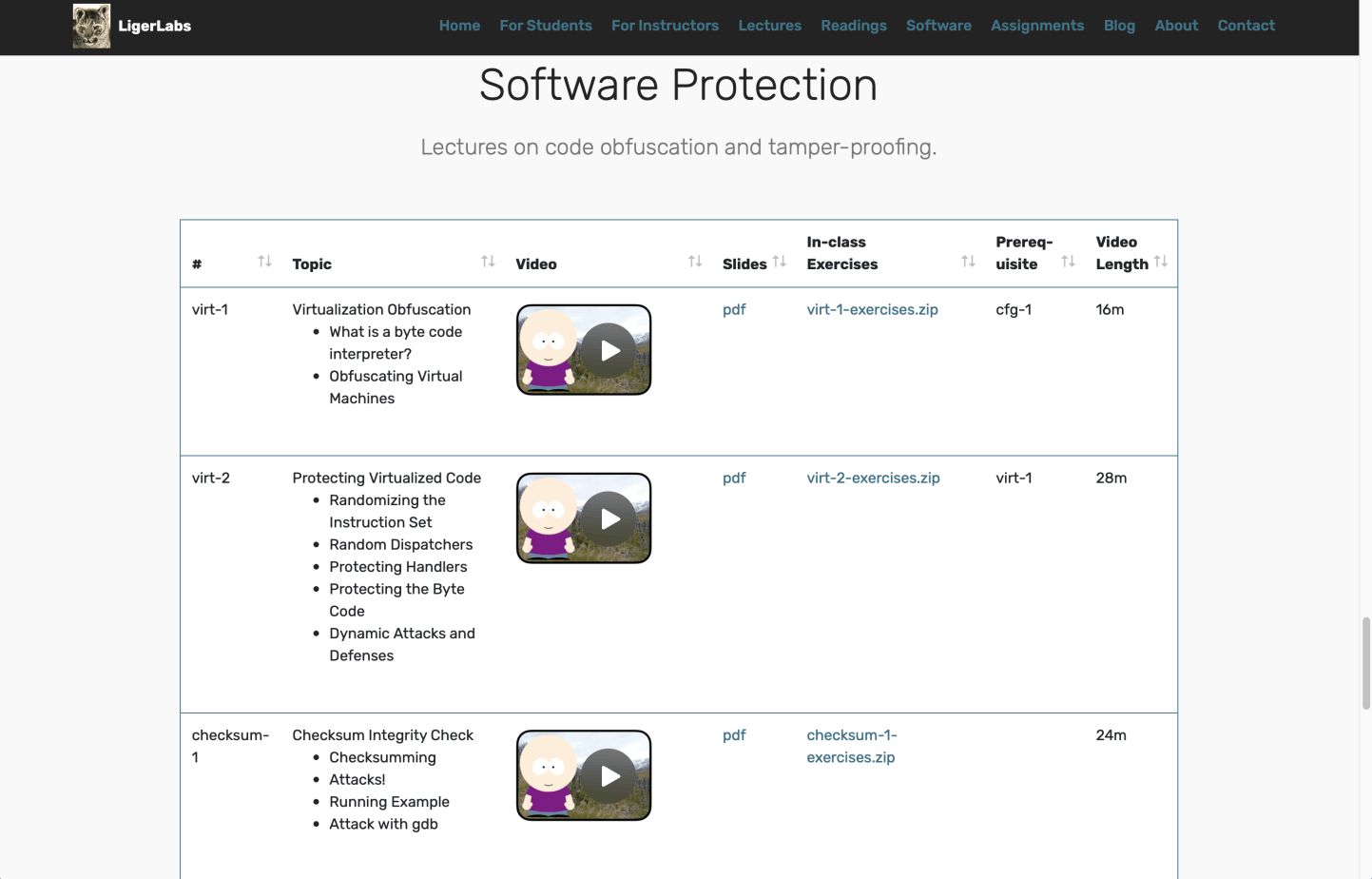
LigerLabs comes with a virtual machine that has all the software you need to get started. LigerLabs also has video lectures covering low-level programming, reverse engineering, and software protection, as well as simple exercises for you to practice your obfuscation and reverse engineering skills:
I often get emails from students telling me "I'm am interested in
obfuscation, please send me the Tigress source code for me to look
at!". First of all, it's not easy learning anything from
the source: 1) you need to know functional programming in general and
OCaml in particular, and 2) you need to become familiar with the Cil
framework on which Tigress is built. A much better way to learn about
obfuscation is to run small C code programs through Tigress and
examine the output programs. Tigress being source-2-source makes
this really convenient, and, after a while, you will start to
figure out how each transformation is constructed.
Now, if you
really are doing serious obfuscation research and would like
to extend Tigress in some way, do get in touch with me. I have shared
the code many times in the past, but I will only do so if
the requests comes from your research advisor, not from
you directly.