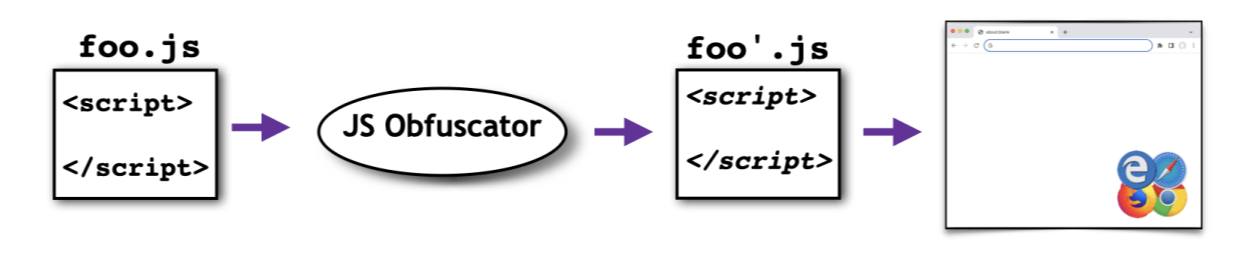
A traditional way to protect a program running in browser is to 1) write the program in Javascript and 2) obfuscate it using a Javascript obfuscator:

An alternative strategy is to 1) write your program in C, 2) obfuscate it with a C-2-C obfuscator like Tigress, and 3) translate the resulting obfuscated code to WebAssembly using the emscripten compiler:
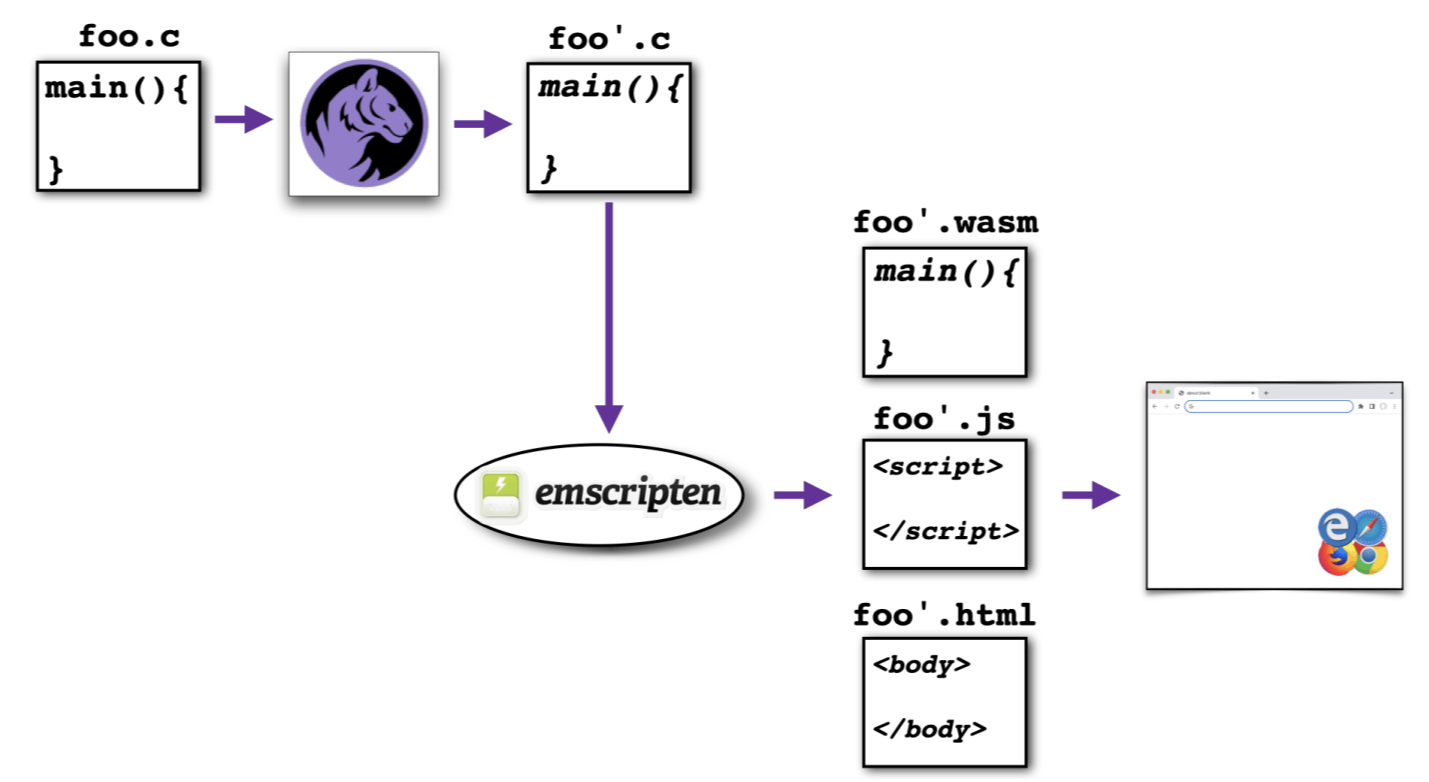
As you can see, emscripten actually produces 3 files, the actual webassembly, a javascript library, and the html file that gets loaded into the browser. Below is an example of how to first obfuscate a C program foo.c with Tigress, and then compile the obfuscated file obf.c with Emscripten to a WebAssembly/html/Javascript package. Note the --Compiler=emcc argument to Tigress which specifies that the WebAssembly compiler (emcc) should be used, rather than the native C compiler:
EMSDKPATH=PATH_TO_EMSDK_INSTALLATION/emsdk/upstream/include/c++/v1
> tigress \
-I $EMSDKPATH \
--Compiler=emcc \
--Environment=wasm:Linux:Emcc:4.6 \
--Transform=Flatten --Functions=fib \
--out=obf.c foo.c
> emcc \
-I $EMSDKPATH \
-O2 \
obf.c \
--emrun \
-o wasm.html \
-s WASM=1 \
-s ASSERTIONS=1 \
-s ALLOW_MEMORY_GROWTH=1 \
-s AGGRESSIVE_VARIABLE_ELIMINATION=1 \
-s ERROR_ON_UNDEFINED_SYMBOLS=0 \
-s USE_WEBGL2=0 \
-s USE_GLFW=3 \
-s FULL_ES3=0 \
-fmacro-backtrace-limit=0
> emrun --browser safari wasm.html