Tigress is a diversifying obfuscator for the C language that supports many defenses against both static and dynamic reverse engineering attacks. To get started, download a version for your platform, and check that the installation was successful:.

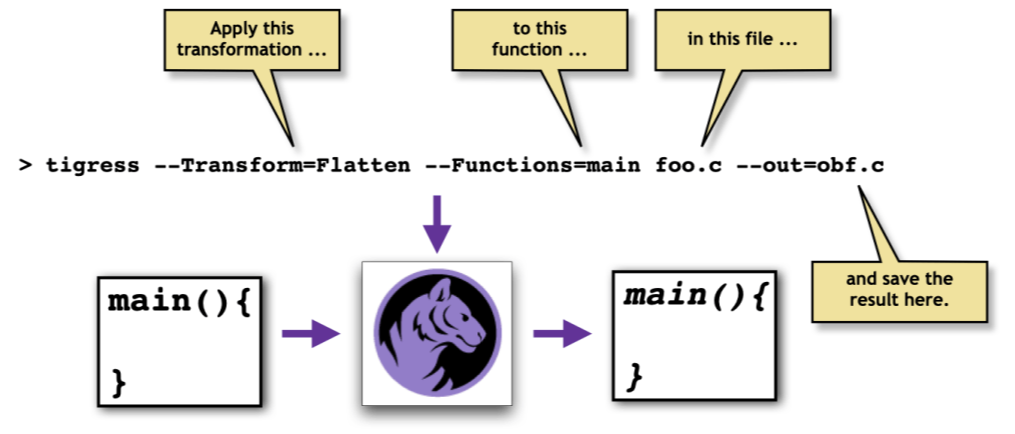
Tigress is a source-to-source transformer - it takes a C source program as input and returns a new C program as output. An obfuscation script (actually, a long sequence of command line options) describes the sequences of transformations that should be applied to the functions of the program. Now you can try out Tigress on a simple example:
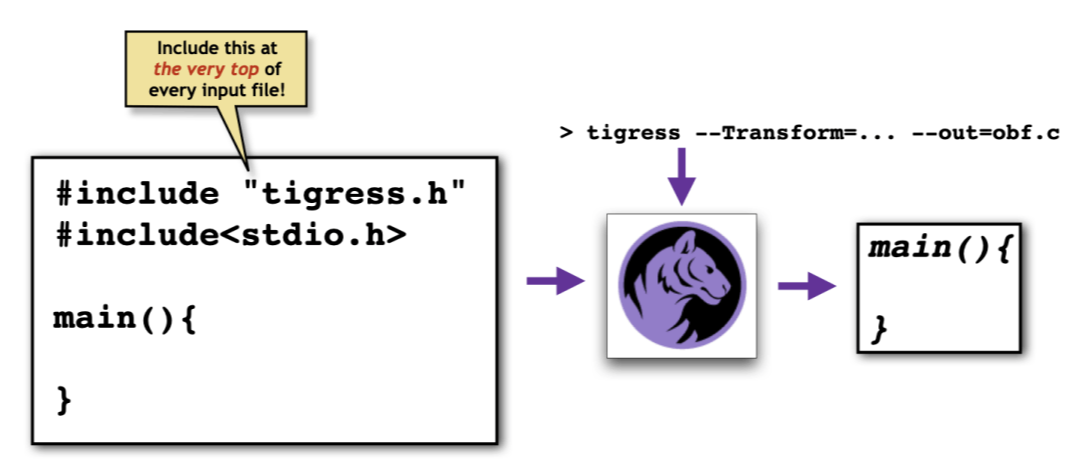
You must include the file "tigress.h" at the top of every one of your input files. You can find this file in the Tigress distribution directory (the location depends on your platform):
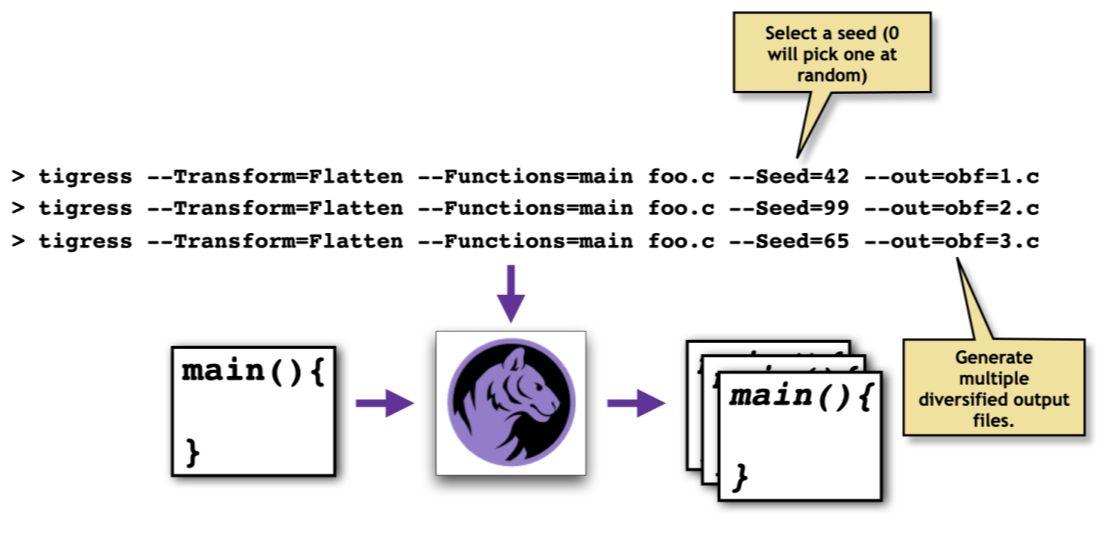
Tigress is a diversifying transformer which means that from a single input program, we can generate multiple different output programs:
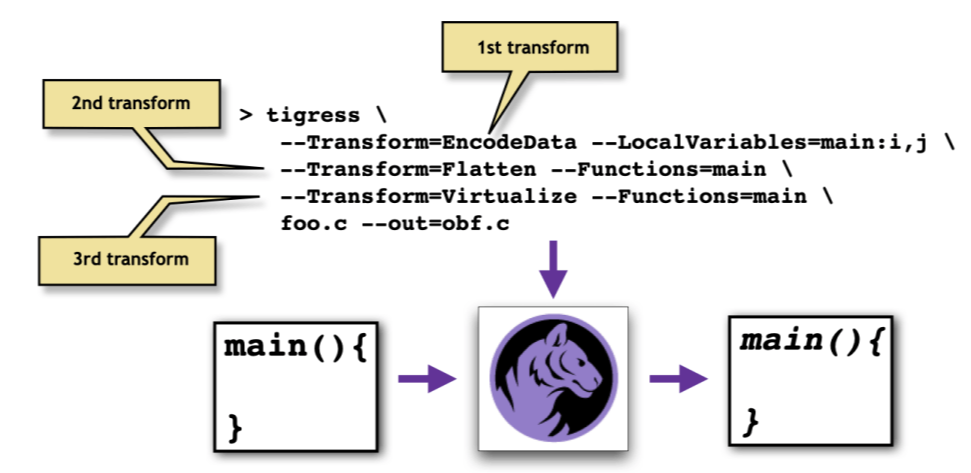
The obfuscation script will typically contain not just one, but a sequence of code transformations. This is necessary to obtain the right level of obfuscation, and to protect your code against different types of attack:
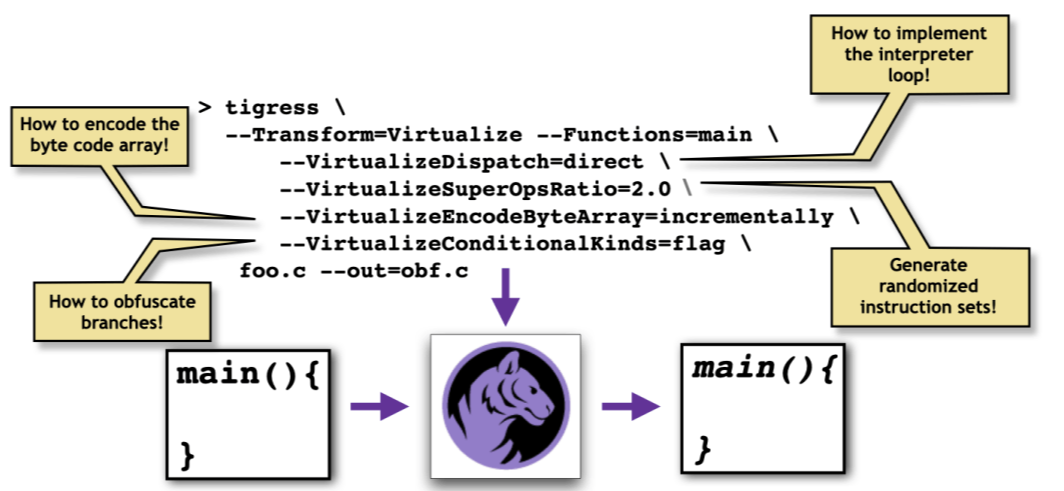
For every transformation there is an (often large) number of options which modify the behavior of the transformation. Choosing a particular list of transforms, and a particular set of options modifying these transforms, is yet another way to diversify the obfuscated code:
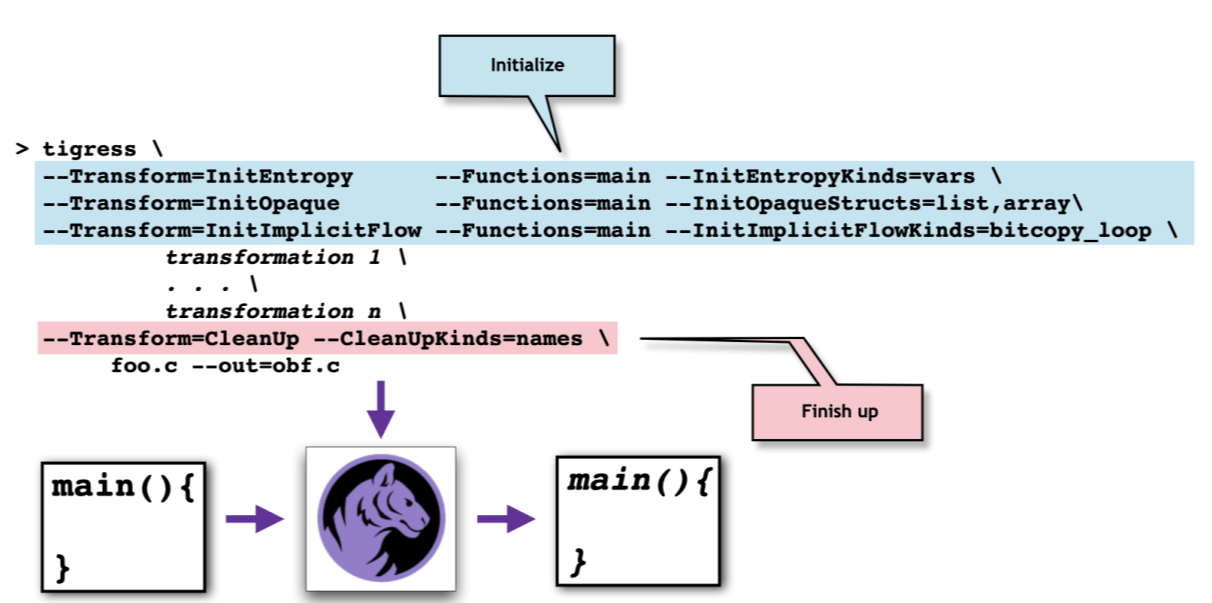
A typical Tigress script contains 1) a list of initialization transformations, 2) the obfuscating transformations themselves, and 3) a final CleanUp transformation. Don't worry about the initialization - when they are necessary, Tigress will let you know! In this example, the CleanUpKind "names" will perform an obfuscation of all the identifiers in the program. This transformation has to be performed last in order not to interfere with other transformations:
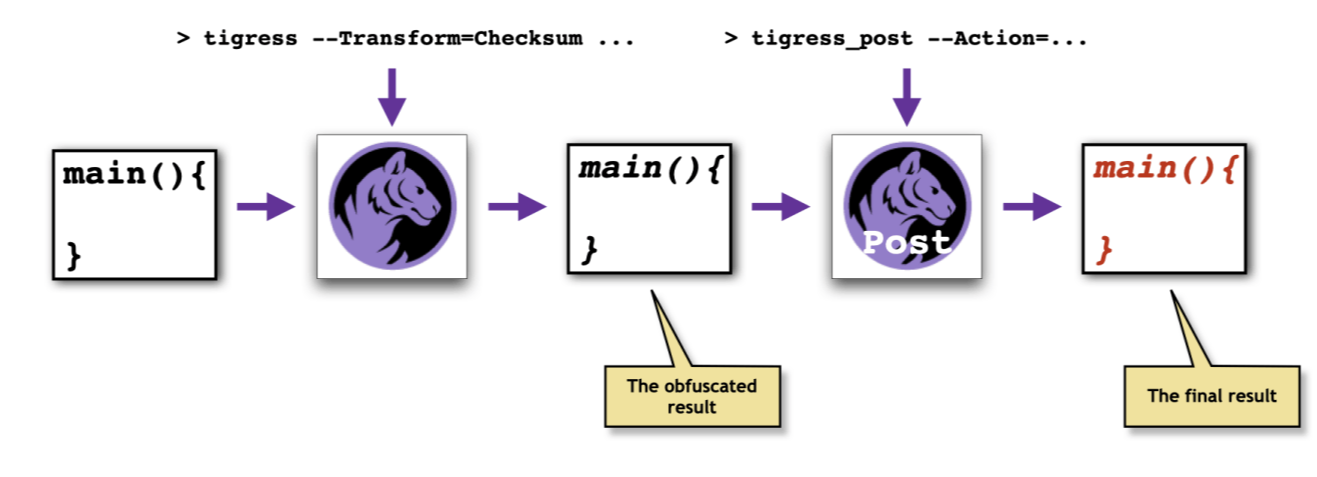
For some transformations, most notably Jitting, JitDynamic, and Self Modify, a source-2-source transformation is not enough. You will have to do some post-processing of the binary file, using the program tigress_post: